By Kate Klein, kklein@nrha.org, and Hilary Welter, hwelter@nrha.org
You’ve read the stories about data breaches, but are the numbers too big to hit home?
In September 2014, Home Depot confirmed that hackers used malware, or software designed to steal digitally stored information, to access payment card information from more than 40 million customers.
The discovery of the breach began a rapid reaction from the retailer’s IT team, and launched a project costing hundreds of millions of dollars to find the breach, increase security and recover from the damage.
“The Company’s IT security team has been working around the clock with leading IT security firms, its banking partners and the Secret Service to rapidly gather facts, resolve the problem and provide information to customers,” Home Depot reported two weeks after discovering the data breach.
This breach hit a massive retailer and garnered extensive media coverage, but data theft is a threat to every retailer. And when small companies are the targets, the damage can quickly put them out of business because they don’t have access to around-the-clock teams to help them recover.
The following numbers should be more revealing of your retail operation’s data security risks. In 2015, 30 percent of data breaches occurred in the retail sector, and 43 percent of those attacks were against businesses with 250 employees or fewer, according to research from Symantec, a data security company.
The danger to small businesses is growing as massive companies, such as Home Depot, invest millions of dollars to beef up their data security.
Small businesses like yours, then, remain more accessible, and become more appealing targets, to cybercriminals.
These data thieves can use methods such as hacking, sending malware via email or data skimming from devices physically attached to credit card readers.
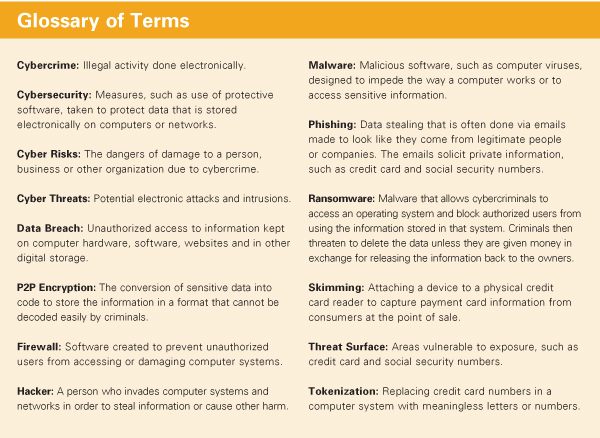
Hardware Retailing spoke with experts from organizations that work with retailers to guard against data theft. Our goal is to provide you with information on the risks you face and practical steps you can take to protect your customers and company.
These experts include Tom Litchford, vice president of retail technologies for the National Retail Federation; Donna Embry, chief payments adviser for the payment processing company Payment Alliance International; and Donald Smith, director of the office of entrepreneurship education at the U.S. Small Business Administration. Visit TheRedT.com/data-security-qa to read online-only Q&As with Scott Reynolds, CEO of Member Insurance, and James C. Trainor, assistant director of the FBI Cyber Division, on ways to help businesses recover from cybercrimes.

For additional resources on securing your business’ data, visit TheRedT.com/security-resources.
Hardware Retailing: Is cybercrime always a constant threat to businesses?
Tom Litchford: I think as long as you have an internet connection, these guys are going to be looking to get in. I think all businesses are
being targeted.
HR: What information should retailers carefully guard against data theft?
Litchford: I think when you look at the retail industry right now, the primary data that the bad actors (cybercriminals) want is your credit card data, because they can take that data and easily monetize it in terms of selling those numbers, creating counterfeit credit cards, using them to buy merchandise.
In retail right now, the big target is point-of-sale systems. I will say, too, the other thing I would be extremely careful with is something called Locky ransomware. What these guys are doing now is embedding their malware in Microsoft Office documents such as Word documents and sending you what we call a phishing email. They get you to bite on this phishing email. You open the Word document, and then next thing you know, you have Locky ransomware, which then basically encrypts all of your system, even network attachments that it can find, and then asks you to pay for them to give you the unlock key.
Donna Embry: Protecting sensitive credit card or debit card data is paramount. If a retailer is doing e-commerce, it’s critical to install firewalls and anti-virus software to protect from hacking or skimming the payment information. In addition to payment card data, any personal data such as social security numbers, passwords or even employment history is vulnerable to use in identity theft schemes. It is important to review website addresses to ensure that false links have not been inserted, so that customers go to the real website and not a pseudo-site. If the retailer uses cellphones for mobile payment, protecting that information is equally important. There are also the back office vulnerabilities that sometimes get overlooked because of the focus on POS or payment data. If a retailer has a personal computer in the back office that’s used for email, financial data or personal information, you’ll want to make sure that it is properly protected.
Donald Smith: POS systems are a main concern, and with migration to mobile payments, customer communications and facility access managed via mobile device, small business owners should think of systems and multiple access points when considering cyber security. Many initial hack attempts are still delivered via simple attempts like phishing scams, instant messaging, phony websites and the like.
HR: Why would a hacker or other data thieves target small businesses?
Embry: The hacker may feel that smaller businesses aren’t on the radar. If a data thief can go to an area and find 10 small businesses that are easy targets under the radar and aren’t paying attention, he or she may choose to hit several small businesses instead of one big company.
If a criminal is putting a skimmer on a machine, they’re doing so because they feel that they can get away with it. Additionally, the press picks up on larger hacks based on the size and scope of the compromise, which leads to increased measures of implemented security features. It really depends on what the criminal is looking for. If they see a way through your business to get to a larger entity such as a processor, they may target you. These crooks are very smart; they do their homework.
Litchford: Large retailers are encrypting data now from the time a card’s swiped to the time it gets to their processor for approval. So the [criminals] can steal that data all they want, but if it’s encrypted, they won’t be able to use it. The other half of that is something called tokenization. Once the processor has the data for approval, they send it back to the retailer in something we call tokenized form so that 16-digit credit card
number is no longer there in the open. When retailers store credit card data, for example, to use for later returns and refunds, they are no longer storing that data in its normal format. They’re storing it in what’s called a token.
So, these are the things bigger guys are doing to remove that threat surface, which then kind of is putting the bull’s-eye on smaller retailers because the [criminals] will go where the grass is greener, where it’s easier to do their fraud. And obviously if something’s encrypted, it makes it harder for them to get that number.
HR: What damage can cybercrimes cause to businesses?
Smith: A cybercrime can compromise business continuity, customer trust and financial resources—all impacting a business’ current operations and the future viability of the business. Take stock of the situation immediately to assess what recognizable actions should be taken, while consulting with additional resources like law enforcement, system administrators, etc. A business may need to temporarily pull some services offline, limit staff access to PCs, and check with its banking partners to see if a crime has resulted in unauthorized transactions.
HR: What are some key identifiers that a business is susceptible to
a cyberattack?
Embry: If your payment process involved a clerk going into a backroom to process a payment and the consumer isn’t in full control of the card, that’s always a signal that the business would be an easy target for card skimming or unauthorized gathering of data.
If you have self-service checkouts, you have to be careful that there are not ways for malware to be put on those systems or skimmers to be added to the devices. Criminals are very good at being able to immediately hack into your systems, so you have to be very careful about how payments are done and how consumers are authenticated.
HR: How do most business owners find out when a data breach has occurred?
Litchford: I would say, most of the time they don’t find out themselves; they find out from other parties—either the FBI or the Secret Service calling them, or Visa calling them. Typically what will happen, from a credit card perspective, is Visa’s fraud alert system will indicate there’s an issue. What they do is triangulate back with their bad cards and say, “OK. It looks to us like all of these fraudulent card activities now seem to originate from a certain date at a certain vendor or a certain retailer.”
HR: How should business owners respond if they learn they are the victims
of cybercrimes?
Smith: To start, a business owner should file a report with their local police to create an incident report and contact their local U.S. Secret Service branch’s electronic crimes unit.
If the crime involves identity theft, the Federal Trade Commission (identitytheft.gov) should also be contacted. Local authorities will also advise of specific actions that may include contacting the Social Security Administration if a social security number has been compromised or even the Department of Motor Vehicles regarding vehicle/fleet registration or ID info.
Litchford: Currently 48 states, plus the District of Columbia, have different laws about how you have to notify your customers. Make sure you have general counsel there for advice on how to do that.
HR: What are some best practices that a business owner should follow to protect data, prevent an attack and be prepared if one occurs?
Embry: Make sure you have anti-virus software on the computers that operate your business. These might not even necessarily be associated with the payment process. Install and maintain firewalls within your system to prevent hackers from getting into data when it is either coming in or going out of your system. It’s also always important to back up your systems so you aren’t vulnerable from having all of your data in one place all the time. A lot of companies require employee passwords or PINs to be unique, change frequently and never be shared. Above all, training and awareness are probably most important. Train clerks to look for suspicious activity. Even while standing in your checkout lane, cybercriminals can be very good at shoulder surfing and gathering information. Being aware of your surroundings and what’s going on can help a lot.
I’d say it’s critical to have a written data security policy. It should include your policy for password changes; how you change your password, how you share the data, how to store the data, what kind of firewall you have, when and where you back up the system.
Litchford: My opinion is they should have relationships with either the FBI or the Secret Service. That would be at a local level. Those would be the two groups I would go after. Their job is to prevent cybercrime and help you recover from cybercrime. And the FBI has the added job of prosecuting them.
 Hardware Retailing The Industry's Source for Insights and Information
Hardware Retailing The Industry's Source for Insights and Information








